In this article, we going to learn how networking works and simple terms in networking. Also, we are going to learn simple network attacks.
This article is suitable for computer scientists, ethical hackers, or anyone interested in IT. Good readings!
What are Computer Networks?
Networks are simply the interconnection of certain things. Connected devices can be various things, like smart light bulbs, phones, computers, smart refrigerators.
Components that are connected and communicate with each other are part of a network.
A network consists of at least 2 devices (something needs to be connected after all). The number of things in the network can reach billions.
Why Networks Important?
When talking about what networks are, most people have in mind why they are important.
Networks allow computers to communicate and access more information (like the Internet). For example, Accessing weather data, controlling the degree with remoter.
Of course, all these good things also have a bad side, Networks can be easily hacked and cause big problems. Network security is an important issue nowadays.
In this article, we will give you information about networks and discuss their weaknesses. Networks are a very important topic for cybersecurity professionals.
Basics of the Internet: Biggest Network in World
There is a network that we use frequently today, we call it the internet. You are accessing the article you are currently reading from a device via the internet.
Internet is formed by connecting small networks (private networks) that are independent of each other with the help of the public network.
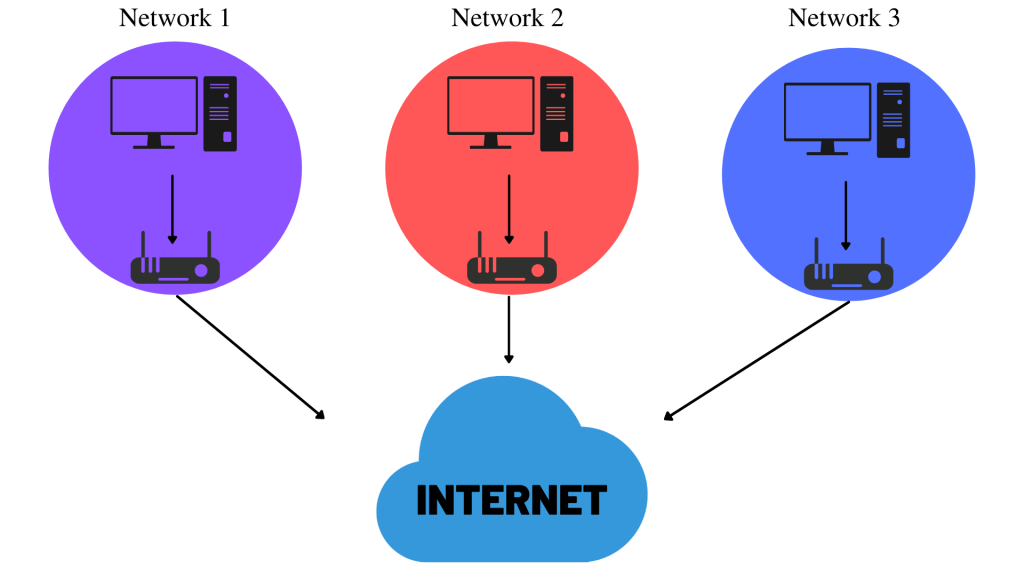
As seen in the picture above, we have 3 hidden networks (can be on different devices instead of computers), while these networks are private in themselves, these private networks are connected to each other with the internet.
If you prefer the private network to share information, you can share information only with devices in the private network, if you prefer the public network, you can shop with anyone connected to that network.
How to Find Devices on The Network?
Nice question, and it’s very simple. We have 2 methods for finding devices, these are the IP (Internet Protocol) address and MAC (Media Acess Control) address.
The IP address is an address used to identify the computer on a network for a certain period of time, while the M.A.C is a unique address of the device.
1 – Ip Adresses
The IP address identifies the computer on the network for a short time, unlike MAC (media access protocol), the IP address can be changed easily.
An IP address is a set of numbers that are divided into four octets, for example, the IP address 192.168.1.1 can be given.
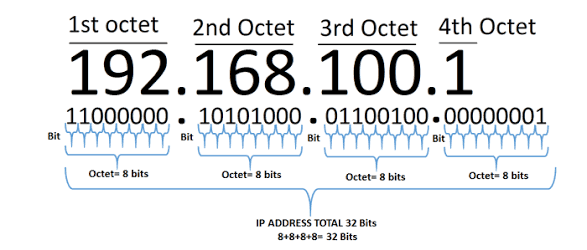
The IP addresses can be changed manually or, automatically with VPN, but two computers with the same IP cannot exist on the same network.
We have two IP address types, these are public and private. The public address is used to identify the device on the Internet.
A private IP address is used for connections with other devices. In other words, your IP address on the Internet and your private network IP address are different.
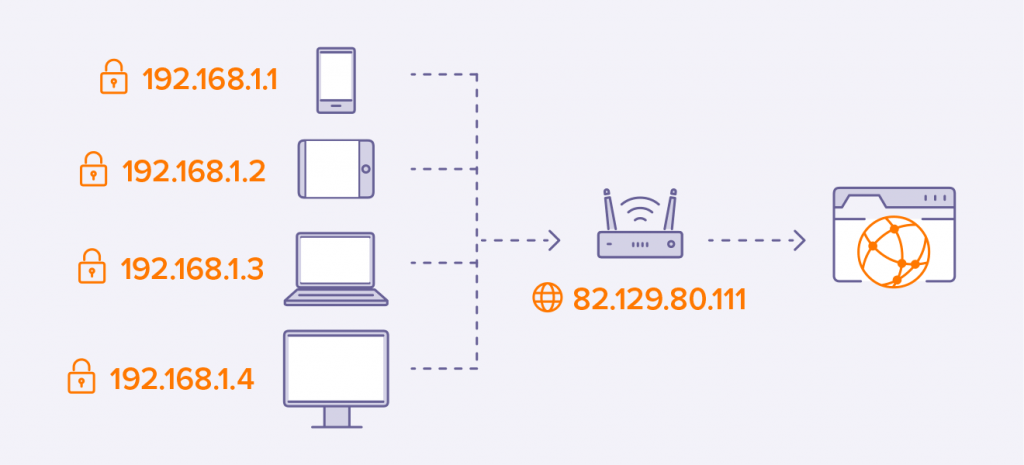
Like the diagram above, every device in the private network uses private IP to communicate with each other, but every device connects to the internet with the same public IP.
Public IP addresses are provided to you by the Internet Service Provider (ISP) for a monthly fee.
2 – MAC Adresses
Every device on the network has a physical network interface. A unique MAC address is assigned at the factory where this network interface is built.
The MAC address is a hexadecimal number consisting of 12 characters. Every 2 characters are separated by “:”, “:” is considered a separator.
The first 6 characters in the MAC address represent the company that made the network unit, while the last 6 characters are a unique number.
MAC Spoofing
Some firewalls use the MAC address to identify users, in such cases, you can masquerade as a different person with MAC address spoofing.
For example, you have a messaging application, and when you message the other party, it checks the Mac address to identify it.
If the 3rd person knows the MAC address of the person receiving the message, they can read the message by adjusting their MAC address according to the target.
Ping and ICMP Packets
A ping is a tool used to determine the performance of the connection between devices. It offers the ping command ready in operating systems terminals.
Ping uses ICMP (Internet Control Message Protocol) packets. The time taken for ICMP packets traveling between devices is measured by ping.
ping 192.168.1.1With the help of the syntax above, you can ping the desired destination (you can modify the packets with different settings)
What is Ping of Death?
A Ping of Death (PoD) attack is when an attacker destabilizes the system by sending malformed or oversized packets with the ping command.
When a maliciously large packet is transmitted from the attacker to the target, the packet is split into chunks, each below the maximum size limit.
When the target machine tries to assemble parts, it exceeds the total size limit and a buffer overflow can occur, damaging the machine.
What is DDOS Attacks?
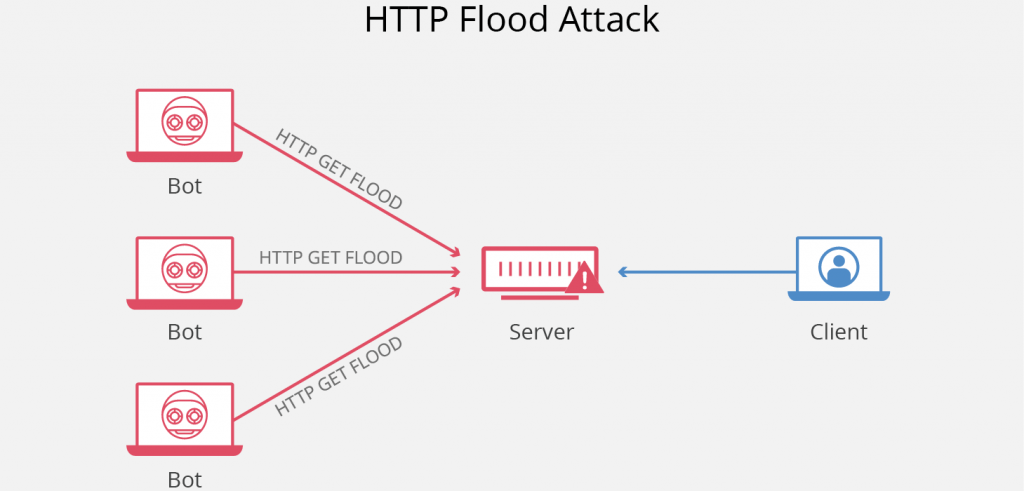
Another attack tool that is frequently used by hacktivists today is DDOS, and we often hear its name today.
If a large number of packets are exchanged from multiple sources to a single destination, it is called DDOS.
Neither DDOS nor DOS attack is done to infiltrate the target, but to damage the target. DDOS and DOS attacks can even damage the hardware.