In this article, we going to learn virtual machines logic and create a one for using ethical hacking.
Cyber security is a growing up industry, and so many people want to enter this industry. This article is prepared to explain the first step.
1 – What are Virtual Machines?
Virtual machines (VMs) are computing resource that uses software rather than a physical computer to run programs and deploy applications.
VM is using CPU, RAM, and disks also virtual machines can connect internet. VMs are existing only code within physical servers.
The virtual machine is isolated from other VMs thus you can run several virtual machines on physical devices.
2 – How to Work Virtual Machines?
Virtual Machine technologies offer using several virtual systems in 1 device. For this firstly, hypervisor manages, separates your recourses for your virtual environments.
While VM working, if the program needs more resources from hardware, the hyper manager schedule requests the physical system’s resources.
This allows the user or program to access the shared pool of physical resources when it needs more resources.
3 – What’s the Benefits of Virtual Machine?
VM has really a lot of benefits, it reduces your spending, also it gives more security, and VM is more portability.
- Hardware costs: Many companies don’t use fully hardware resources (probably, you don’t use too) so organizations can spin up virtual servers instead of investing in another server.
- More Security: VMs are isoleted from main OS, so if you do mistake in VM, you can react quickly.
- Quick recovery: VM offer snapshot feature, this feature help you when your Vm is crush. You can recovery with snapshot.
- Secure Testing: You can test programs and software in VM. Suspicious software should be run on the VM to cause less damage.
These are a few benefits of virtual machines. VMs have more benefits, also Vms are developing and updating every month thus VMs stay up to date.
4 – Virtual Machine Softwares
We have many choices as virtual machine software. In this article, we’ll use Oracle Virtual Box but in this chapter, we’ll show alternative softwares.
1 – VMware Workstation Player (Linux and Windows) – It’s Paid
2 – VMware Fusion (Only Mac) – it’s Paid
3 – VirtualBox (Windows,Linux,Mac) – it’s Free
4 – Red Hat Virtualization (Windows and Linux) – It’s Paid
5 – Boot Camp (Only Mac) – It’s Free
These are the most popular software for virtualization. In my opinion, VirtualBox is a very good choıisen for beginners and who work with multiple devices.
5 – Install ISO File or Install OVA File
Before creating a virtual system, you need ISO or OVA file containing the operating system we want.
ISO file is is an archive file that contains an identical copy (or image) of data found on an optical disc, like a CD or DVD.
OVA files are used by virtualization programs to store various files associated with a virtual machine (VM).
if you do install an iso file, you have to create a new virtual machine from zero however, the OVA file comes with default settings so you don’t need setup.
In this article, we are going to set up Kali Linux OS. You may find ISO and OVA links below.
ISO File Link: Current Version 2021.3
OVA File Link: Current Version 2021.3
6 – Setup Your Attack Virtual Machine With OVA
Kali Linux is mostly used for ethical hacking and cyber security. In this chapter, we are going to create a Kali Linux machine with an OVA file.
After installing Oracle Virtual Box and OVA file, we are ready to start creating attack machines. Click “import” for importing the default machine from OVA.
A panel should appear asking you to locate the OVA file, it looks like the image below. You don’t need to change the source box.
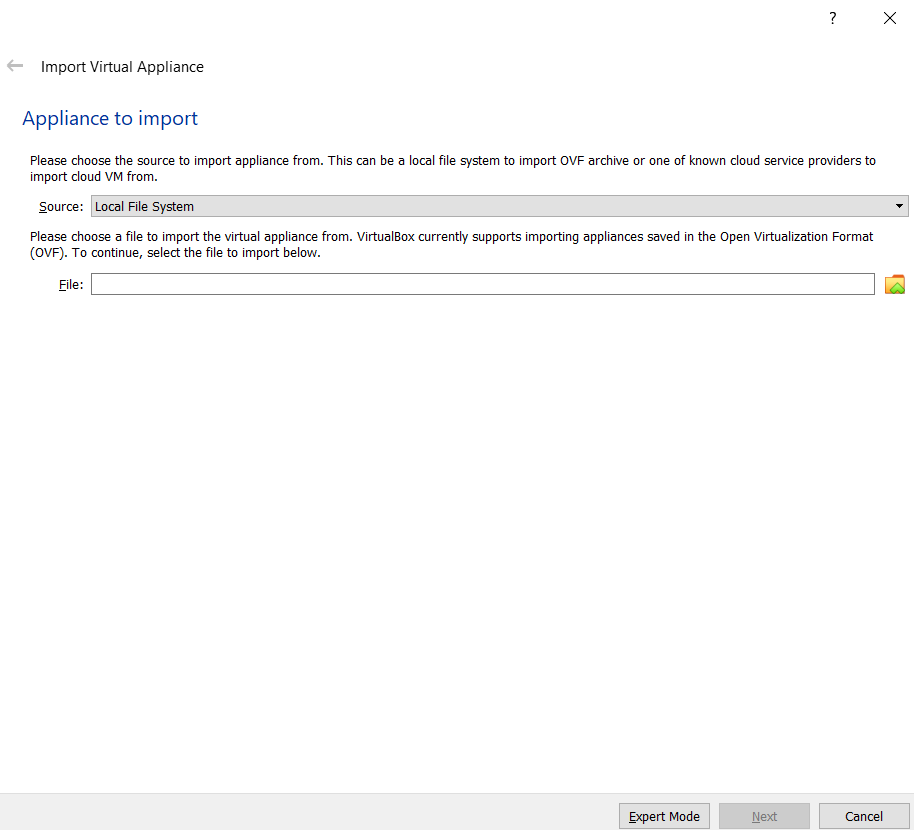
You can type your OVA file path or select the file in Windows Explorer by clicking the “folder button” next to the text box.
After selecting your OVA file, you should see the appliance settings menu. That’s menu is so important for your device and virtual machine.
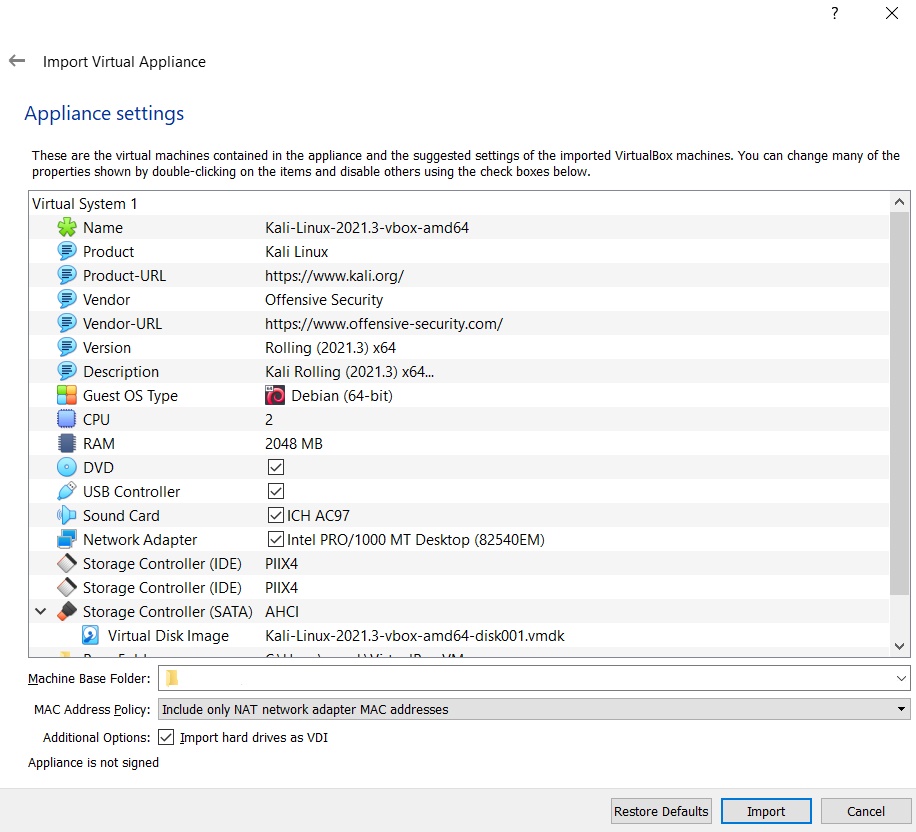
Your virtual machine preferences it’s changeable by your system requirements. But I am to suggest setting RAM 4096 Mb also you can use CPU value 4 instead of 2.
If you want to change your virtual machine path, you can in the Machine Base Folder part. I prefer other settings to be the default.
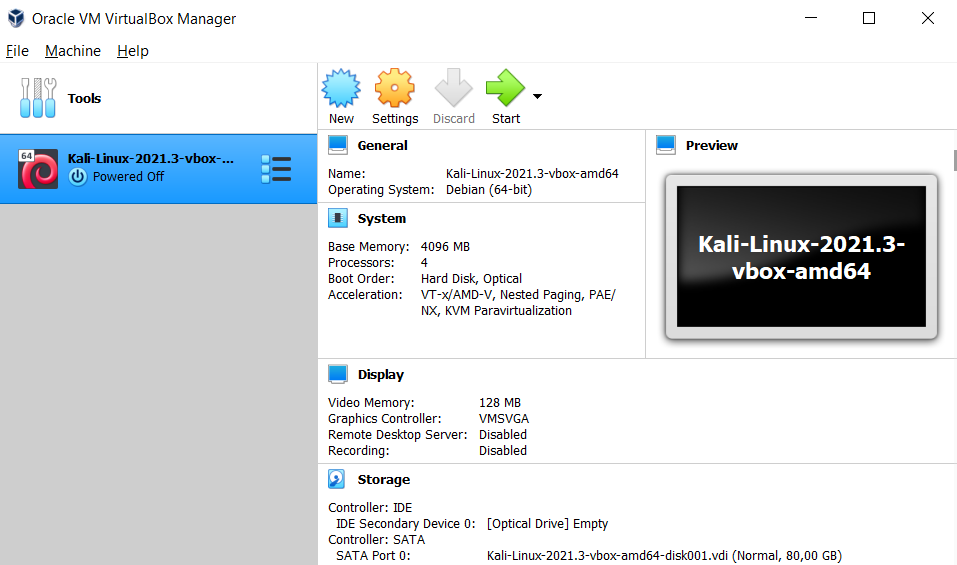
After import, your virtual machine is ready for starting. You can change system settings in the settings menu.
Also, you can set the name of your virtual machine in again settings menu. I suggest setting a name to VM while working on multiple VM’s it will be helpful to you.

You can set the window size in the view menu. Your default username and password is kali. After installation, you can change.
Congratulations, you finished your first virtual machine in Oracle VMBox. If you are select the ISO file for creating a virtual machine continue to the next part.
7 – Setup Your Attack Virtual Machine With ISO
Instead of directly importing a virtual article, creating it yourself from scratch with an ISO file may seem a bit more complicated.
First, make sure your ISO file is installed and start VirtualBox. Welcome Page should you see.
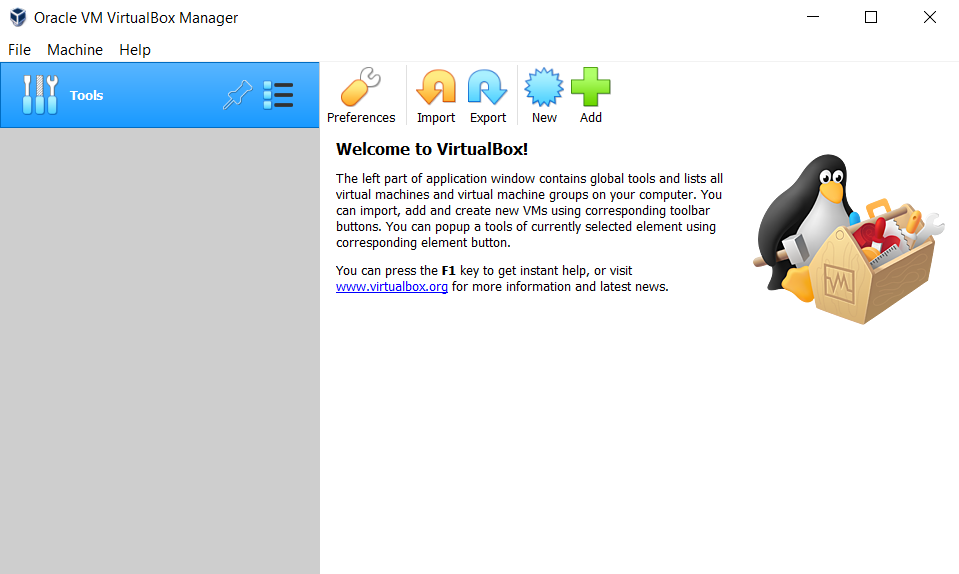
Click the new button, it will open create virtual machine menu. You have to set the virtual machine name, version, and path folder.
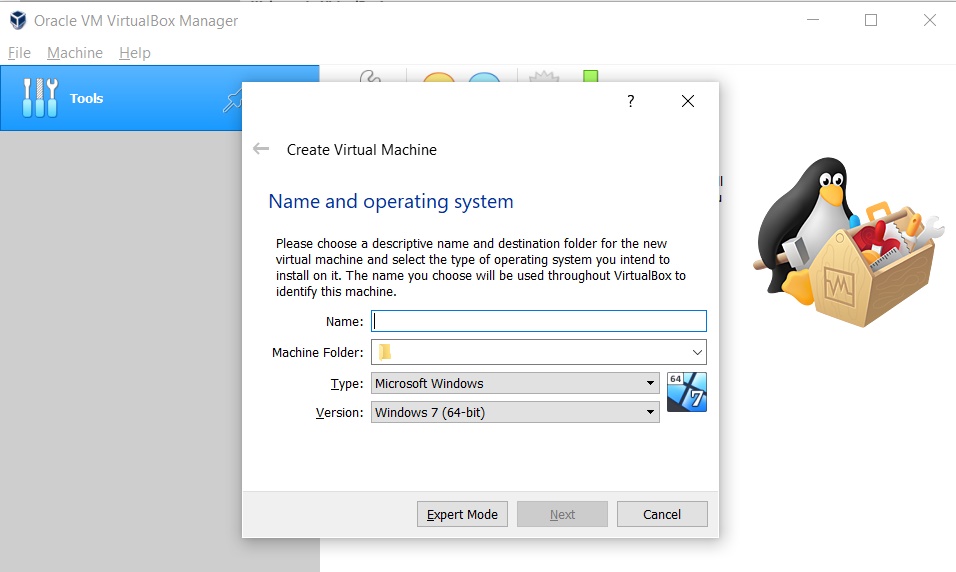
You have to set Linux type after that you must select Debian 64bit version. Next, you can change the machine folder path.
After giving the name and setting version and type. You should see the memory size amount.
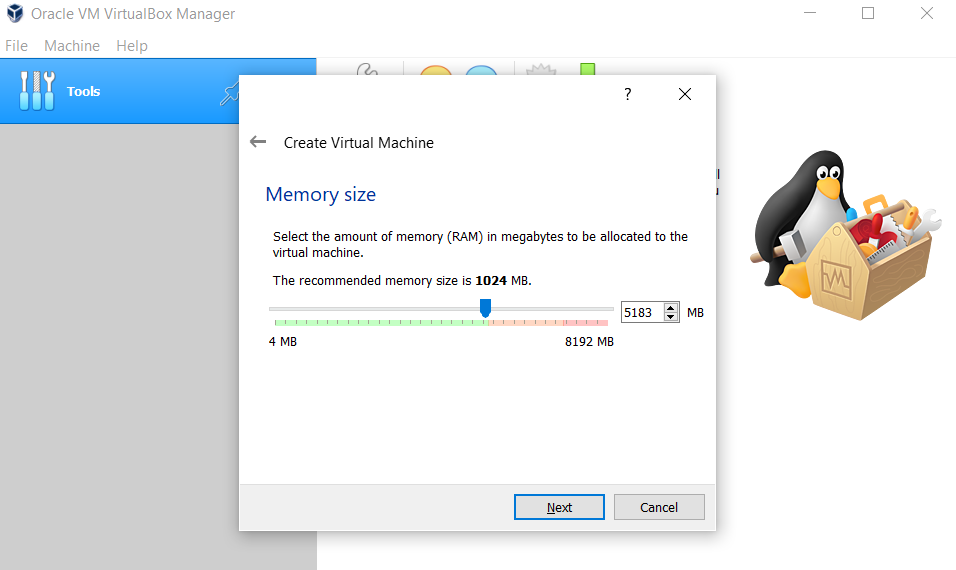
In my opinion, you should separate a minimum of 4096 MB of your Ram. But if you have 4GB Ram or less, you can change size according to your ram size.
Suggestion: If you have 4GB Ram, you can use 3.5Gb of your Ram but you shouldn’t use any application other than virtual machine applications in your device.
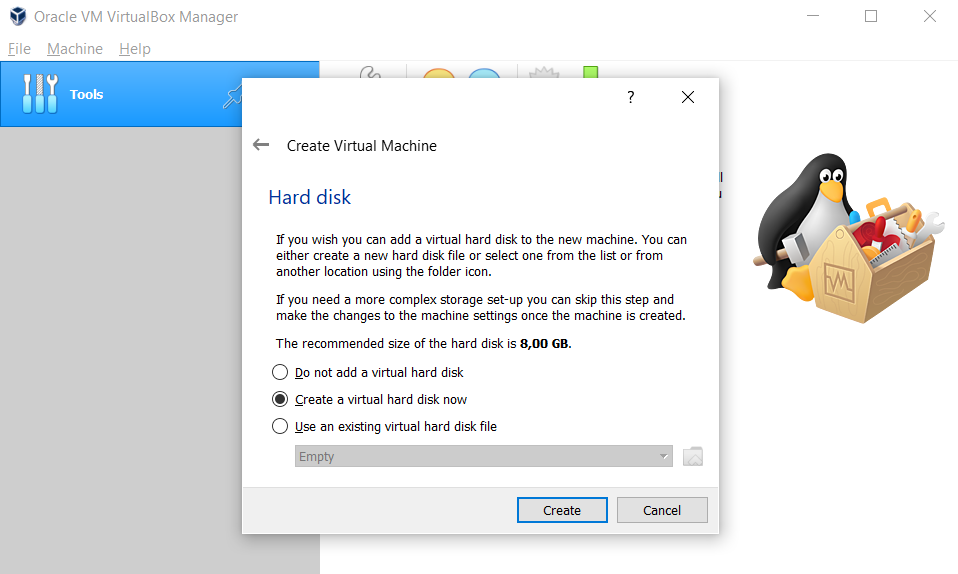
We will use a VDI when creating your Hard Disk space, which means we will allocate a certain space on your hard disk for virtualization.
Firstly, select Create a virtual hard disk right now, After that, you should select VDI (we use this). You will have two options dynamically allocated and fixed size.
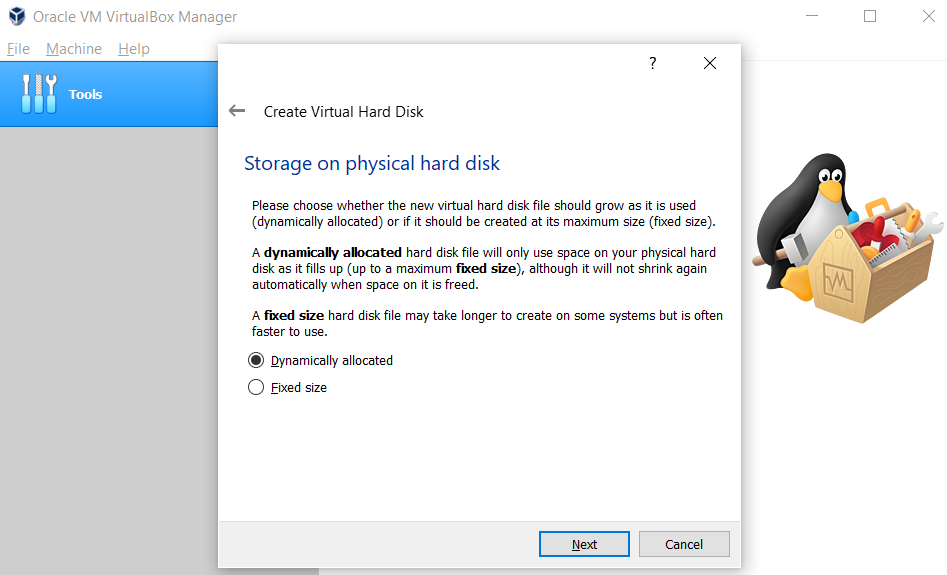
Fixed Size: No matter how much you use the hard disk, as much space is reserved from the hard disk as you specify.
dynamically: if you have set 100Gb but you are using 1Gb, 1Gb space is created from the hard disk, then it grows in the allocated space as the usage increases.
In dynamically Even if you delete 10Gb after using 30Gb, it does not reduce to 20Gb again. 30Gb remains constant, only allowing expansion, not shrinking.
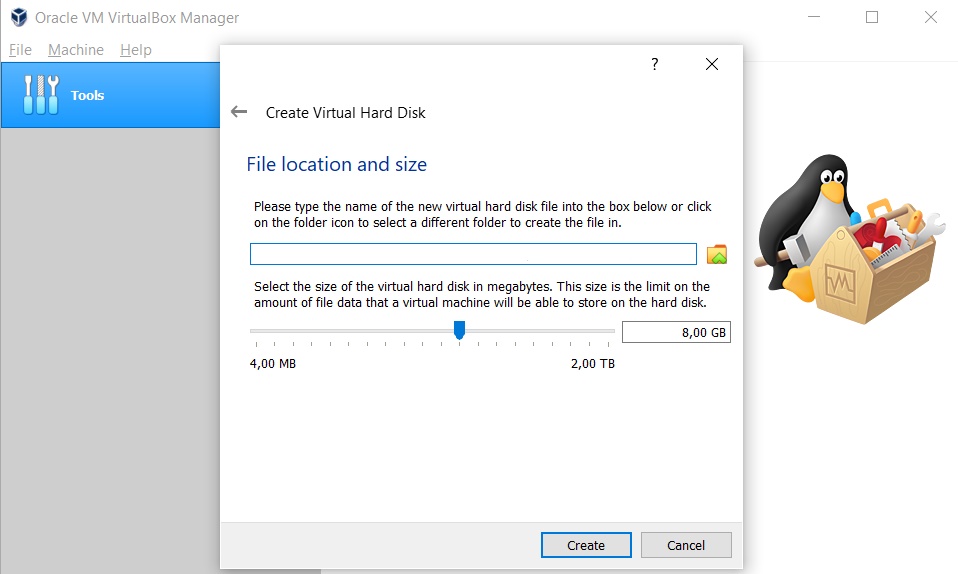
Generally, Kali Linux has not required a big hard disk size but if you work with the big source you can select 50Gb or 100Gb Space.
After creating the hard disk, if you want more storage for your files or any things, you can increase hard disk storage on virtual machine settings.
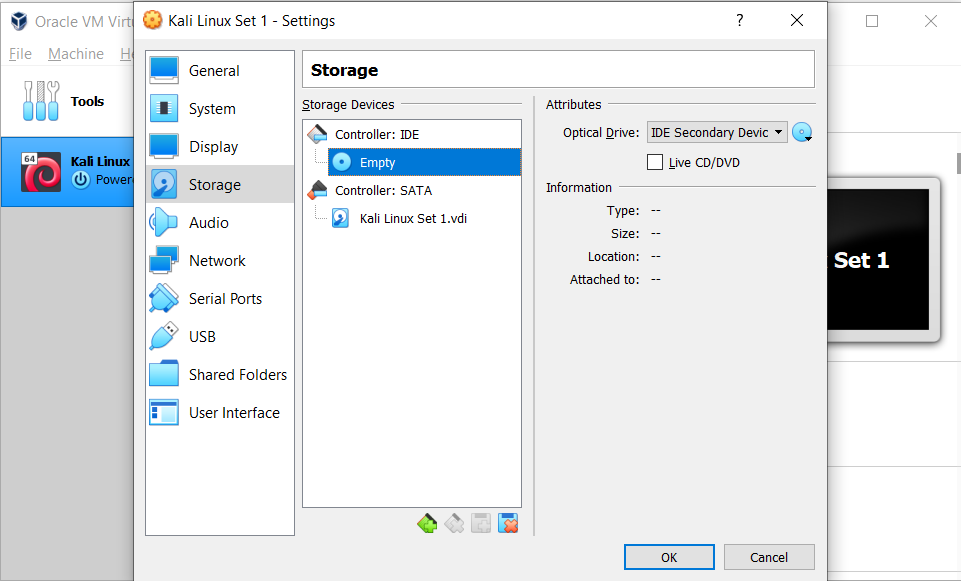
When creating storage, you are ready to add an ISO file on the virtual machine. Select the settings menu and click Storage subparts.
Click the disk button near the Optical Drive text box. Click choose a disk file from the pop-up window and choose your ISO file.
Anymore, you can install Kali Linux OS. You just have to wait for the operating system to install according to your preferences.
8 – Creating Target Machine (Test Machine)
We now have a system where we can write code, do research, and hack. Now it’s time to create a testing machine.
Test machines or target machines are operating systems that have vulnerabilities to improve your skills. They are perfect for penetration testing.
Note: don’t hack your device. Hacking an up-to-date operating system is difficult for beginners and can make your system unstable.
Windows and Linux OS List
Windows Vista is relatively easy to hack, with the drawbacks of being outdated. If you are just starting penetration tests, it may be your first choice.
Linux (Old Versions) Although it is more difficult to hack than Windows, beginners can try to hack older versions.
If you’re intermediate, you can try to hack not-so-old systems like Windows 7 and Windows 8 (it will still challenge you)
Download Old Version Application
When you finish the installation of the operating system, do not start hacking directly, install applications to adapt to the real world.
Installing software can also make your job easier by taking advantage of software vulnerabilities to take yourself further in hacking.
Using VulnHub For Creating Target Device in VM
Vulnhub offers hackable virtual machines. It offers it as an OVA file, so you can import it directly.
Let’s make a small warning, run the systems found here only in your virtual machine and do not allow access to any network.
When you install it by default, it will be securely installed on the virtual box (get more detailed information from the site).
Conclusion
In this article, we have seen how to install Kali Linux, the popular penetration testing operating system, in two different ways and to create target machines.
This article is for informational purposes, My Master Designer is not responsible for any problems or damages that may occur.
